XKeyscore and Data Interception via Submarine Cables: A Global Mass Surveillance System
Since Edward Snowden’s revelations in 2013, the NSA’s XKeyscore program has become synonymous with mass surveillance. This data analysis and search system allows intelligence analysts to access vast amounts of real-time or stored information. One of the main channels for this data collection relies on intercepting communications transmitted via submarine cables, which are crucial infrastructures for global connectivity.
What is XKeyscore?
XKeyscore is a program used by the National Security Agency (NSA) to analyze vast databases containing emails, browsing histories, VoIP calls, online chats, and many other types of digital communication. According to Snowden’s leaked documents, it allows analysts to perform targeted searches on individuals or groups based on criteria such as email addresses, keywords, phone numbers, or suspicious online behaviors.
Submarine Cables: A Priceless Source of Data
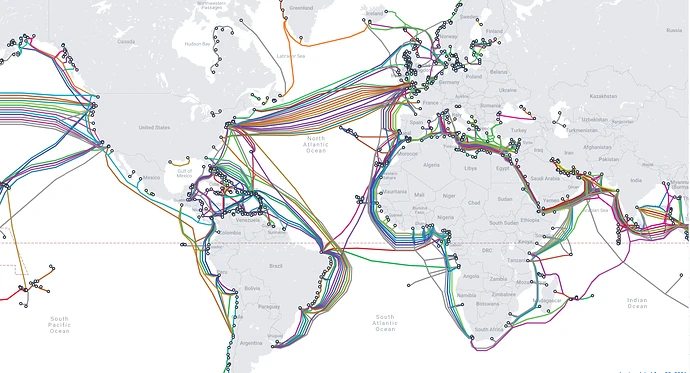
More than 95% of the world’s Internet traffic passes through fiber-optic submarine cables, connecting continents and facilitating data exchanges between businesses, governments, and individuals. These cables are therefore prime targets for intelligence agencies seeking to tap into international communications.
Through partnerships with telecommunications companies and covert surveillance operations, the NSA and its allies, particularly the UK’s GCHQ, have established mechanisms to siphon off data flowing through these cables. Programs such as GCHQ’s TEMPORA specifically target submarine infrastructures to capture vast streams of information before they are processed by analysis centers like XKeyscore.
Interception Methods and Implications
Submarine cable interception is carried out mainly through two methods:
- Landing Stations: Where submarine cables connect to terrestrial networks, eavesdropping and data duplication equipment can be installed.
- Underwater Listening Stations: Some covert operations involve placing interception devices directly on cables underwater, enabling discreet data capture.
The implications of this surveillance are far-reaching. Governments justify these practices by citing counterterrorism efforts and cybersecurity. However, privacy advocates argue that such activities constitute a massive intrusion on individual freedoms with little democratic oversight.
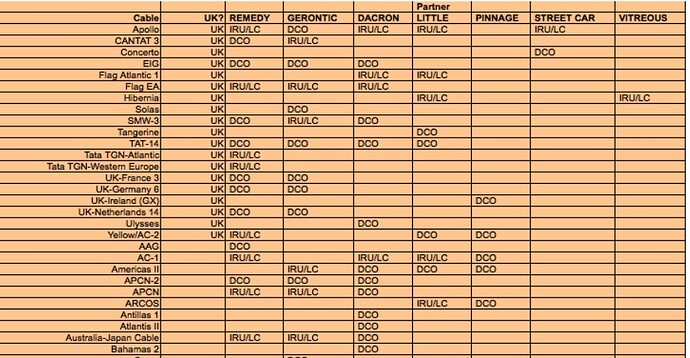
cables locations where NSA have access
Examples of Documented Interceptions
- The TEMPORA Program (UK): Operated by GCHQ, TEMPORA collects vast amounts of internet data directly from submarine cable infrastructure, sharing insights with the NSA.
- Operation Echelon: A global surveillance system believed to intercept satellite and fiber-optic communications for intelligence purposes.
- AT&T and NSA Partnership: Leaked documents have shown that telecom giant AT&T provided the NSA with direct access to its fiber-optic networks, enabling mass data collection.
see :
ISJLP_V3N3_411.pdf (1.5 MB)
Towards Enhanced Security Measures?
In response to these revelations, various initiatives aim to strengthen communication security. End-to-end encryption, the development of independent networks, and improving submarine cable security protocols are some of the measures explored to prevent unauthorized data access.
Nevertheless, mass surveillance remains a reality, and XKeyscore continues to be a powerful tool in the hands of intelligence agencies. Time will tell whether efforts to counter these interceptions will be sufficient to ensure greater privacy in global communications.
Source : https://www.youtube.com/watch?v=2P3P5OkGt8Q&t=1410s
Thanks for reading this, i know it’s not perfect and Xkeystore is old and we don’t know if they really use this now or have new tools